Building HIPAA-Compliant Healthcare Apps in .NET on AWS (with HealthLake FHIR)
Ambareesh Marimekala
9/7/20258 min read

Healthcare applications deal with some of the most sensitive data - a patient’s health information. In the U.S., this is protected by HIPAA (Health Insurance Portability and Accountability Act). For .NET developers, ensuring HIPAA compliance means not just writing code, but building secure systems that respect privacy at every layer.
In this blog, we’ll break down what HIPAA requires and how to meet those requirements in .NET, with diagrams and real-world coding practices.
What is HIPAA?
HIPAA establishes national standards for protecting Protected Health Information (PHI). If you’re storing, processing, or transmitting PHI (names, diagnoses, prescriptions, lab results, etc.), you must ensure confidentiality, integrity, and availability.
Key Rules:
Privacy Rule → Patient rights over PHI
Security Rule → Safeguards (admin, technical, physical)
Breach Notification Rule → Report incidents
Healthcare applications deal with highly sensitive information: patient demographics, diagnoses, prescriptions, and reports. Any unauthorized access can not only harm patients but also result in multi-million dollar penalties under HIPAA.
For developers, this means security-first design — encryption, access controls, and auditing — all built into the application stack.
Think of HIPAA as four big buckets:
📜 The Core HIPAA Rules
Privacy Rule 🔒— "Who can see what."
This rule is about patient control. You can only share a patient's protected health information (PHI) for very specific reasons, like for their treatment, for billing, or for healthcare operations. Even then, you should only share the absolute minimum necessary information.
Example: A nurse in a hospital ward can look at the medication history for the patients in her ward, but she should not be able to see the billing information for patients in another part of the hospital.
Security Rule 🛡️— "How you keep it safe."
This is the technical side of HIPAA. It requires you to have strong administrative, physical, and technical safeguards to protect electronic patient data (ePHI). This is where your engineering work comes in, including things like setting up user authentication, encryption, and logging.
Example of an Administrative Safeguard: A clinic trains all new staff on HIPAA policies, including how to handle patient information and how to spot phishing emails. Every six months, they conduct a mandatory security training session and a simulated phishing test to make sure everyone's knowledge is up-to-date.
Example of a Physical Safeguard: A hospital has a server room containing patient data that can only be accessed by authorized IT staff using keycard access. All workstations in patient rooms are configured to automatically lock after five minutes of inactivity to prevent unauthorized viewing.
Example of a Technical Safeguard: A healthcare app requires doctors to use a unique username and password, along with multi-factor authentication (MFA)—such as a code sent to their phone—before they can access patient records. All data sent between the app and the server is secured with encryption (TLS) to prevent hackers from intercepting it.
Breach Notification Rule 🚨— "If something goes wrong."
If unsecured patient data is exposed or stolen, you must notify the affected patients quickly—no later than 60 days after you discover the breach. If the breach affects a large number of people (500 or more in a state or region), you also have to inform the federal government (HHS) and the media. A good practice is to encrypt all patient data; this can protect you from having to report a breach if the stolen data is unreadable.
Small-Scale Breach Example: A nurse accidentally emails the unencrypted medical records of 20 patients to the wrong recipient. After discovering the error, the hospital must immediately notify all 20 patients and explain what happened. They are not required to notify the media or HHS immediately but must log the incident and report it to HHS annually.
Large-Scale Breach Example: A hospital's network is compromised by a cyberattack that exposes the personal health information of 5,000 patients. Because this number is over the 500-person threshold, the hospital must notify all 5,000 affected patients, report the breach to the HHS, and also notify major media outlets in the affected state or region within 60 days of discovering the breach.
The "Encryption Saves the Day" Example: A doctor's unencrypted laptop containing PHI for 1,000 patients is stolen from their car. This is a reportable breach. However, if that same laptop's hard drive was fully encrypted, and the encryption key was not also on the laptop, the data would be considered unusable and unreadable by the thief. In this case, the hospital would not have to issue a breach notification because the information was not "unsecured."
Omnibus/BAA & Enforcement 🤝— "Who's on the hook."
A Business Associate Agreement (BAA) is a legal contract that third-party companies must sign if they handle patient data for you. This includes cloud providers like AWS, managed service providers, or billing companies. The Enforcement part of this rule means there are penalties for not following the rules, and these penalties can be severe depending on how negligent you were. This is why it's so important to train your staff, document your policies, and prove that you are following them.
BAA Example: A medical practice wants to use a new cloud-based service to manage its billing. The service provider will be handling patient payment information and other data. Before they can legally start, the medical practice and the cloud provider must sign a Business Associate Agreement (BAA). This contract ensures the cloud provider agrees to follow HIPAA rules and is legally responsible for safeguarding the patient data they handle.
Enforcement Example: An IT company is contracted by a hospital to manage its servers. The company fails to apply security patches for several months, leading to a ransomware attack that compromises patient data. Because the company signed a BAA, they are liable for their negligence. The HHS’s Office for Civil Rights (OCR) investigates and can impose a civil monetary penalty. A real-world example is the University of Rochester Medical Center, which paid a $3 million settlement for a similar violation after an unencrypted laptop was stolen, years after a previous breach. This shows that negligence and a repeated lack of safeguards can lead to substantial fines.
⚙️ The Security Rule in Simple Terms
The HIPAA Security Rule is broken down into three main categories of safeguards you need to have in place:
1. Administrative Safeguards (People & Process) 👥
This is all about the human side of security and the policies you put in place.
Risk Analysis & Management: Figure out what could possibly go wrong and create a plan to reduce those risks.
Policies & Training: Have clear rules for your team, conduct regular training, perform phishing drills, and have a plan for what to do during an incident.
Vendor Management: Make sure all your partners have a signed BAA and that you only give them the minimum access they need to do their job.
2. Physical Safeguards (Real-World Access) 🏢
This focuses on securing the physical location where data is stored and the devices used to access it.
Access Control: Limit who can get into offices, server rooms, and other secure areas.
Device Security: Make sure computers have screen lock and auto-logout features. Properly and securely destroy old hard drives and other storage media.
For Remote Work: Ensure remote laptops are secure, have mobile device management (MDM) software, and use encrypted disks.
3. Technical Safeguards (What You Build) 💻
This category covers the digital protections you build into your systems.
Access Control: Use unique user IDs for everyone, and require Multi-Factor Authentication (MFA) and session timeouts.
Audit Controls: Keep detailed logs of who viewed or changed patient data, and when they did it.
Integrity: Implement measures to prevent data from being tampered with and to detect any unauthorized changes.
Transmission Security: Make sure all data sent over a network is encrypted using a protocol like TLS (Transport Layer Security), so it's never sent in plain text.
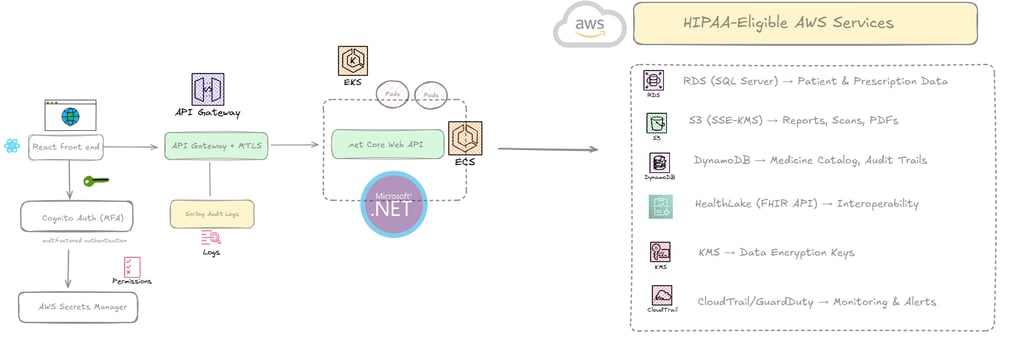
Building a HIPAA-Compliant System with AWS & .net
When it comes to building healthcare applications, keeping patient data safe is the top priority. The great news is that you don't have to start from scratch. Amazon Web Services (AWS) is a "HIPAA-eligible" cloud provider. This is a crucial distinction—it means that while they provide the secure tools, it's still up to you to use them correctly. The first step is to sign a Business Associate Agreement (BAA) with AWS. Think of this as a legal contract where AWS promises to protect the data on its side, making you and them partners in compliance.
🛠️ Key AWS Services for Your Healthcare App
For .NET developers, AWS offers a powerful toolkit to handle everything from user authentication to data storage, all while staying HIPAA-compliant.
Amazon RDS: This is where you can store all your structured patient information, like their name, age, and insurance details. Think of it as a super-secure database where all the records are encrypted, so only authorized people can read them.
Amazon DynamoDB: Need to quickly look up prescriptions or other patient metadata? DynamoDB is a fantastic choice for fast, simple lookups.
Amazon S3 with SSE-KMS: This is your digital filing cabinet. It's the perfect place to securely store all your unstructured data, like lab reports, X-rays, and patient PDFs. The built-in encryption, managed by AWS Key Management Service (KMS), ensures these files are locked down.
AWS HealthLake: This is a specialized service built just for healthcare data. It’s a secure, FHIR-compliant data store that lets you organize, standardize, and analyze all your patient information. It’s a game-changer for interoperability, making it easier to share data between different healthcare systems.
AWS KMS & Secrets Manager: These services are like a high-tech bank vault for your most sensitive information. KMS helps you manage the encryption keys used to lock up your data, while Secrets Manager keeps your passwords and other sensitive information safe and sound.
AWS CloudTrail & GuardDuty: These are your digital security guards. CloudTrail keeps a detailed log of every action taken in your AWS account, so you always know who accessed what and when. GuardDuty is an extra layer of protection, constantly monitoring for suspicious activity and alerting you to potential threats.
🩺 Case Study: Patient Records & Prescription Management
To see how all these pieces fit together, let's imagine we're building a new Healthcare Portal. This portal will be the central hub for doctors, nurses, and pharmacists, allowing them to:
Store patient records: Securely save demographic details like a patient’s name, age, and ID.
Manage prescriptions: Keep a clear and organized record of all prescriptions and medications.
Handle lab results: Easily upload and store digital lab reports and imaging files.
View patient history: Let staff securely access a complete and accurate history of a patient’s health records.
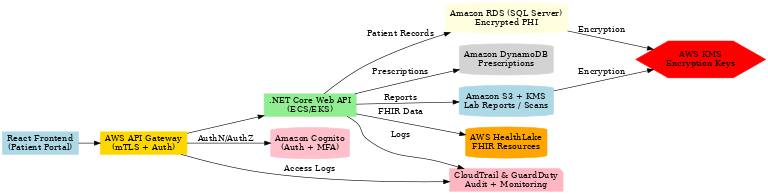
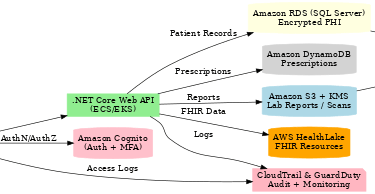
🔑 HIPAA Controls in the .NET + AWS Stack
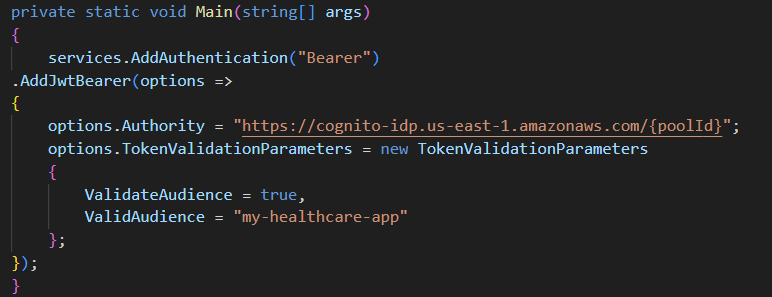
1. Authentication & Authorization with Cognito
Cognito enables multifactored authentication and RBAC polices as well.
Each role (Doctor, Nurse, Pharmacist) has least privilege access.
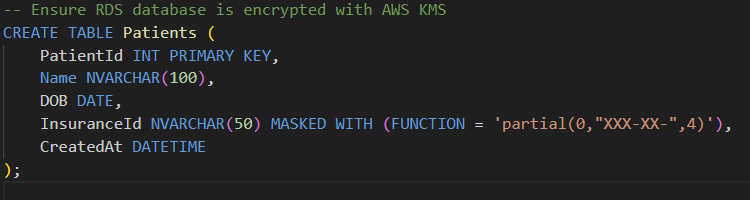
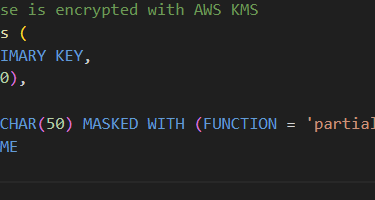
2. Storing Patient Records in RDS with Encryption
Use Always Encrypted / TDE in SQL Server (RDS).
Sensitive fields (SSN, Insurance ID) are masked or encrypted.
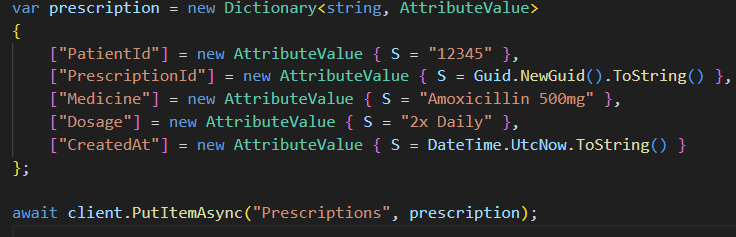
3. Prescriptions in DynamoDB
Fast lookup for current & past prescriptions.
Scalable NoSQL access pattern.
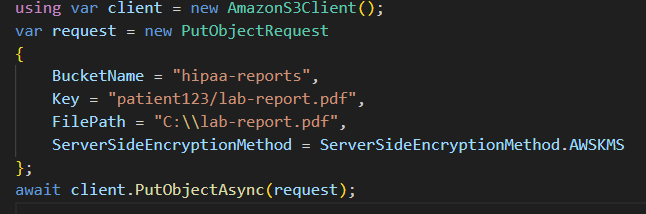
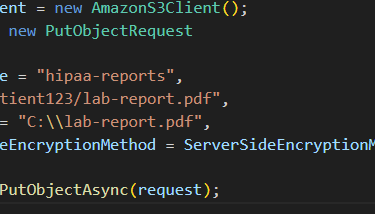
4. Lab Reports in Encrypted S3
Reports stored in S3 with SSE-KMS encryption.
Access controlled by IAM roles (doctors only).
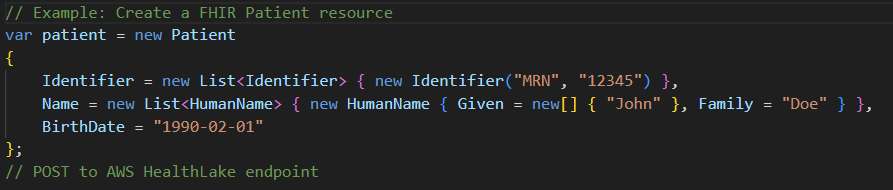
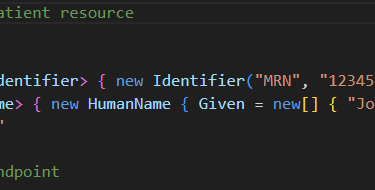
5. FHIR Interoperability with AWS HealthLake
Store structured patient data (conditions, medications, allergies) in FHIR format.
.NET can integrate with HealthLake APIs via standard FHIR SDKs.
Conclusion
HIPAA compliance in healthcare is about security + trust. By combining .NET’s strong framework for authentication, logging, and encryption with AWS’s HIPAA-eligible services, you can build a scalable, secure system for managing patient records, prescriptions, and reports.
The key is to embed HIPAA controls at every layer: API, database, storage, and monitoring. Done right, your healthcare app will not only meet compliance requirements but also earn the trust of doctors, patients, and regulators.